I’ve been annoyed at some of the things in the computer science and, more specifically, computer security community for a long time, and decided to finally write them down. This has become quite a wall of text. Depending on how you read this, this may be a rant or a plea.
A few days ago, when I was browsing the website of a security conference (SEC 2014 in this case, but this is applicable to a lot of conferences), I became curious. Shouldn’t a conference focussing on “Applied Cryptography”, among other things, automatically forward me to the HTTPS version of their website? I changed the http:// to a https://, and OH GOD WHAT THE HELL?
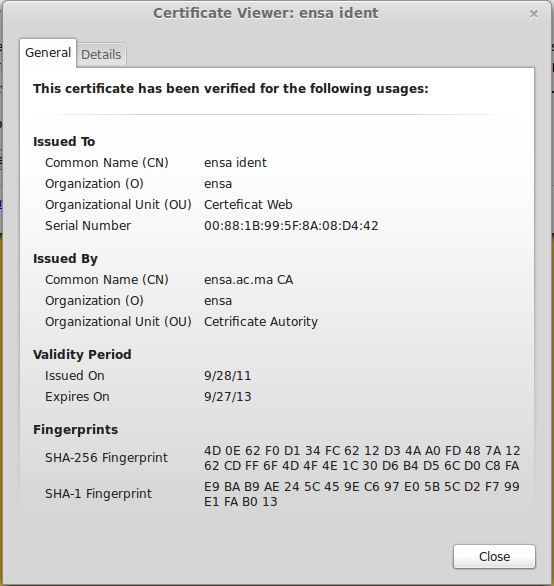 Interesting. A self-signed certificate, expired for more than three months, and with a Common Name of “ensa ident” (as opposed to, you know, the domain name it was supposed to protect).
Interesting. A self-signed certificate, expired for more than three months, and with a Common Name of “ensa ident” (as opposed to, you know, the domain name it was supposed to protect).
Well, someone must’ve been sleeping, I figured, so I went to the contact page of the website, and OH MY GOD WHAT THE HELL?

A hotmail address. Not only that, but a hotmail address with no information about a PGP key for secure communication.
Now, some people may ask “so what?”. To which I reply: How can the security community as a whole condemn bad security practices and demand secure, end-to-end-encrypted communication for everyone, if the organizers a conference that attendees pay between 250 and 550 € to attend can’t get their shit together enough to at least provide a valid, well-formed SSL-certificate for their websites. Hell, I’m not even asking for one that is signed by a proper CA. I can live with a self-signed certificate, but at least put in the effort to have the CN match your domain name and to create a new one once the old one has expired.
As for the PGP key: I can understand if conferences do not provide a PGP key because their contact address is actually a mailing list that sends the message to multiple people (although it is beyond me why, in 2014, there is no program that will decrypt all incoming messages and re-encrypt them with the keys of the recepients of the mailing list. Or, if there is such a program, why no one uses it). But this is a hotmail.fr address. This is bad on so many levels. A conference on “Information Security Education” can’t even afford to have their own eMail address?
I regularily annoy companies by writing them eMails closing with “P.S.: Have you ever considered adding the capability to receive encrypted eMails to this address? [Link to a tutorial]”. Some ignore this, some make excuses. I only know of two companies who allow me to send them encrypted eMails. One of them is my bank, who will then reply unencrypted with a full-quote, rendering my encryption worse than useless. The other are the people at Uberspace.de, who I am not a customer of, but who provide their key prominently on their website.
How can I keep a straight face demanding this of those companies if the people running our conferences are too lazy or just plain don’t care enough about the ACTUAL TOPIC OF THEIR CONFERENCE to take the 30 minutes to set something up? How can I keep a straight face if, until a few months ago, I could write encrypted eMails with more of my parents (2) than other computer scientists I regularily mailed with (1)?
The general reaction if I propose mail encryption to the average CS student is one of the following:
- I should totally do that, but it’s too much work
- I’m not writing anything secret, so why would I encrypt it?
- I don’t know anyone who is using mail encryption
- I’m not writing any mails anyway, I’m using Facebook to talk to other people.
To which I would reply, respectively:
- It’s 30 minutes of work, once, and then you can have it up and running until you reinstall your system. How is that “too much work”? Don’t you value your privacy enough to invest 30 minutes into protecting it?
- Because it is good practise to encrypt it. Because, even if you don’t write any secret letters, you would still not be happy to have other people read them (hopefully).
- Then be the first and pester your computer scientist friends. Take them to a crypto party. It’s gonna be fun.
- …Goodbye. *shake head, go away, loose faith in humanity*
It is not about the contents needing hiding. It is not about keeping something from the NSA (although that’s an awesome side effect). It is about making encrypting communication a social norm, at least within the computer science community.
At 30c3, I received three business cards. Two of them were from people working for the Tor Project (Roger Dingeldine and Jacob Appelbaum). Both of them had their PGP Fingerprints printed on their business card. This is what I want to see. Get away from “here’s my eMail address” towards “here’s a way you can send me an encrypted message and be sure you reach me and no one else”.
The third business card was from a nice woman of maybe 50 years with barely any background in computer science. She wanted to help an open source project, so she got a ticket to 30c3 and went to different assemblies and workshops (which, in itself, is pretty awesome, I might add). I recently sent her an eMail, signing it with my PGP key, as I always do for those mails. I received an encrypted response, stating that she had just started using GnuPG and Enigmail and asking if I would help her set up a laptop with Linux and full disk encryption.
If 50-something year old executive consultants can figure this our, why can’t the security community?